I’ve got some down time, and after that last article i’m looking to start sharpening my privilege escalation. Follow enough hackers on twitter and you’ll hear about Hack in the Box.
Their entrance exam is really straightforward and it still stuck me. Too many months pretending I’m not a pentester gave me brain lock when I hit it. I did the basics, I viewed source, tracked down something that looked super important, inviteapi.min.js. Just from the filename I knew it would be minified javascript, so an extra inscrutable version of a language I barely comprehend. I remembered enough tricks to get the one line of gibberish nicely formatted into what resembled a program(not really, browser dev tools just do this for you now!).
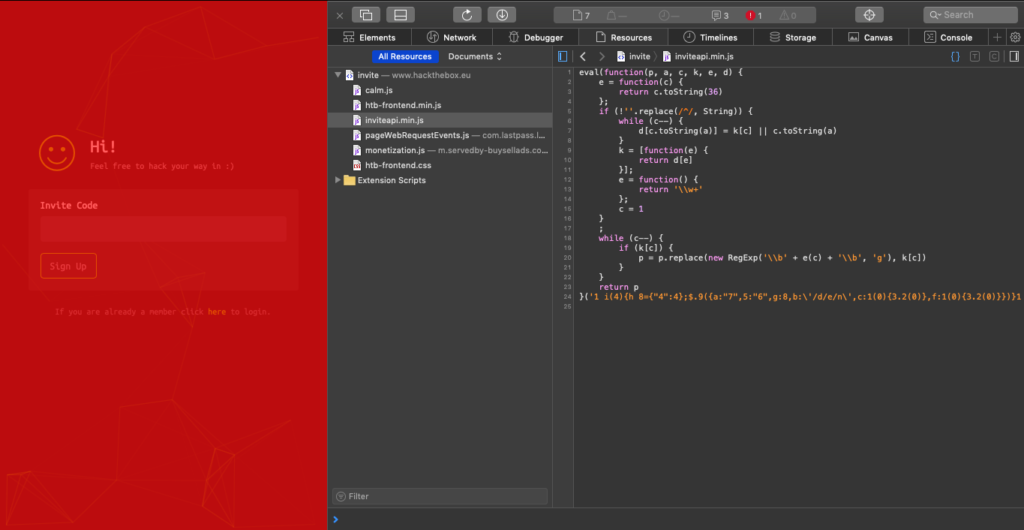
Then stuck. So what does every good hacker do when they’re stuck? Try and cheat. You guys don’t do that? You should. Super rewarding. As is often the case, some kind soul has not only surmounted this incredible challenge, but they’ve done a great, great writeup about how they did it. Thanks, Billy!
So it turns out that this string is a function. I’m still not hip enough on javascript to understand that part of it, but he’s right.
A little hacker humor, and magic of modern browsers and I’m following along step for step.
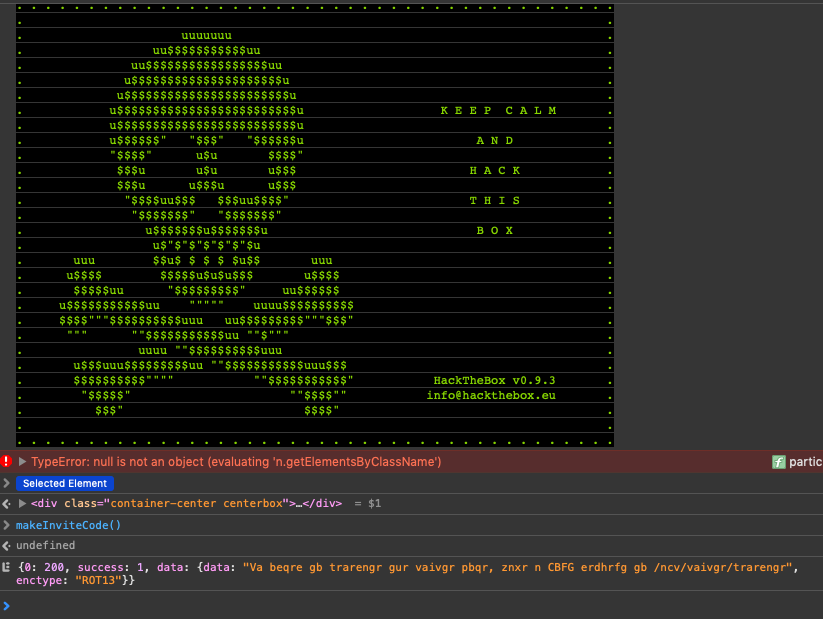
I know how to un-ROT ROT13 gibberish, and from there it was a matter of plug and play.
So getting my feet wet again, i didn’t learn enough javascript to do this on my own. But i did do the work. I look at this like a drill, or a warm up to get the blood moving, access those synapses that have lapsed in the last few months while i managed elementary school birthdays, family vacations, children’s illnesses, and reading a bunch of books about cooking and finance.
